If your agency has done any research on cybersecurity lately, especially as remote work has become more prevalent, you have probably seen people discussing the various pros and cons of using a VPN for government agencies and contractors. While a VPN has plenty of advantages, it can be difficult to understand exactly what a VPN can do and how it works to keep data safe.
We’ve broken it down here–including why you might use a VPN for government work, relevant cybersecurity regulations to keep in mind, and what the future of VPNs and remote government work might look like–so you have all the information needed to decide if a VPN is right for you and get started.
SHOULD YOU USE A VPN FOR GOVERNMENT WORK?
FIRST, WHAT IS A VPN?
A VPN, or a virtual private network, extends a private network across a public internet connection. This gives the VPN user privacy and anonymity online anywhere in the world.
VPNs are able to mask your internet protocol (IP) address by creating a point-to-point data tunnel between your local network and an exit node elsewhere, causing it to appear as if you’re in another location. VPNs also use secure, encrypted connections to scramble any data sent over a public network, making it unreadable to those outside the private tunnel the VPN creates.
These things combined make your actions online essentially untraceable, hiding your browsing history and web activity. When using a virtual private network, the only thing a web server can see is the address of the VPN server, which can be set to appear thousands of miles from where you are actually located.
There are two ways to use VPNs: with hardware or with software. With hardware, the VPN runs on a single, standalone device, which includes a dedicated processor. This VPN setup offers high levels of security, but there are limits to the number of tunnels that can be created and it requires more complex maintenance. Software VPNs, by contrast, run on a server and have a lower upfront cost. Plus, they can be downloaded and set up in just minutes.
VPNs came out just a little over a decade after the birth of the internet. The origins of these private networks can be traced back to 1996, when Microsoft employees first created the point-to-point tunneling protocol (also known as peer-to-peer tunneling protocol, or PPTN). Since then, they have become an essential tool for many, especially as remote work has become more commonplace across all sectors of the workforce. Lately, VPNs for government agencies and contractors are especially popular, as they help protect sensitive material in day-to-day operations online.
WHY YOU SHOULD USE A VPN
To put it simply, VPNs make the internet a more secure place for whatever data you may be processing. They allow employers to safely give employees access to important information over the internet and make each individual user less vulnerable to hackers or data breaches.
Online crime is one of the fastest-growing security threats in the United States. There was a 141% increase in the number of records exposed by data breaches between 2019 and 2020, with expectations that this number will only go up in the years to come. This means that now more than ever, it’s important to use every tool available to protect your privacy.
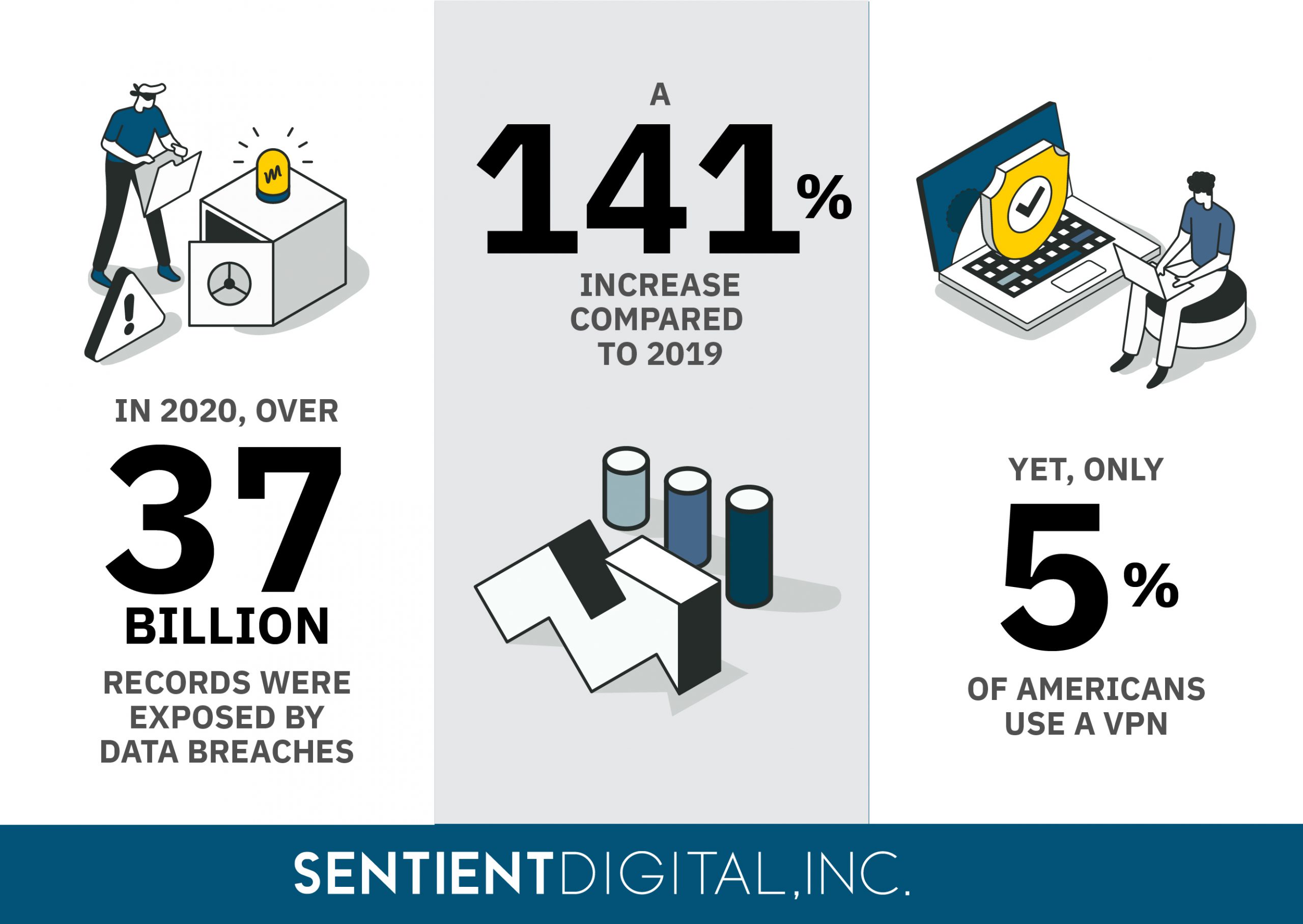
Despite the rise in data breaches, only 39% of Americans use VPNs to protect their online information. By comparison, the countries with the highest VPN download rates in 2023 were Singapore (19%), UAE (17%), and Qatar (15%) . The number of VPN users across the world has gone up recently and is projected to continue growing.
It’s especially important to note that 2020 saw 42% of the United States labor force working from home. This, combined with the continued rise in cybercrime, means that agencies and contractors alike should consider using a VPN for government work.
RULES TO FOLLOW WHEN USING A VPN FOR GOVERNMENT WORK
If you’re thinking about using a VPN for government agency or contractor purposes, you should consider that there may already be a specific set of laws or regulations that govern your transmission of data. The laws and minimum requirements depend on two aspects of the data: the type and sensitivity of the information.
The types of data that government workers or contractors may have to work with include:
- Intellectual property
- Health data
- Personally identifiable data
- Financial data

Government employees or contractors may also find themselves handling various security clearance levels for confidential information and data. This includes but is not limited to:
- Top Secret Information: The highest classification, defined as information that could cause “grave damage” to national security.
- Secret Information: The second highest classification, which would cause “serious damage.” Most classified information falls into this category.
- Controlled Unclassified Information: This data is unclassified, but still not meant for public disclosure.
With that in mind, there are a few existing regulations that must be followed by those working for the government on any level. This is a brief breakdown of the most relevant rules in place for those considering a VPN for government-related work to keep in mind.
1. THE NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY (NIST) FRAMEWORK FOR IMPROVING CRITICAL INFRASTRUCTURE CYBERSECURITY
This is the standard by which government agencies and contractors measure their cybersecurity posture. Anyone who deals with government data must prove they comply with NIST at a minimum.
2. THE COMMERCIAL SOLUTIONS FOR CLASSIFIED (CSFC) PROGRAM
Established by the NSA/CSS, the Commercial Solutions for Classified Program was created to allow commercial products to be used for transmitting and handling classified NSS data while keeping it secure.
3. NATIONAL INFORMATION ASSURANCE PARTNERSHIP (NIAP) CERTIFICATION
NIAP certification is primarily used to certify commercial technology and products that can be used to deal with all classified data. It is mandated by federal procurement requirements for use in the United States National Security Systems.
4. THE DEFENSE FEDERAL ACQUISITION REGULATION SUPPLEMENT (DFARS)
This is a set of restrictions used in Department of Defense (DoD) applications that protects the U.S. defense industry from becoming dependent on foreign supplies. The specific clause related to cybersecurity is DFARS 252.204-7012, which focuses on cybersecurity controls (including safeguarding defense information and cyber incident reporting) that should be in place for those who contract or supply the DoD.
5. THE CYBERSECURITY MATURITY MODEL CERTIFICATION (CMMC)
From the Department of Defense, this certification piggybacks off the previously mentioned DFARS. The Cybersecurity Maturity Model Certification (CMMC) calculates cybersecurity maturity based on three levels (in CMMC 2.0), along with a corresponding set of processes and best practices to be put in place depending on the sensitivity and classification of the information being protected.
Frequently Asked Questions About a VPN for Government Settings
Can my VPN be tracked?
Because a VPN encrypts your data, it is extremely unlikely to be tracked by your ISP or other third parties besides the VPN itself. However, the trustworthiness of your VPN is paramount. VPNs may have varying policies and technical vulnerabilities, so your agency must do adequate research before choosing your VPN software. Also, make sure to check for and download software updates when available.
What is the difference between a business VPN and a personal VPN?
A business or B2B VPN is designed for organizational settings, while a B2C VPN is created for use by individuals. Most relevantly for government agencies, B2B VPNs allow employees to work remotely while protecting work-related private information. Companies can control and monitor employee’s web activity, making it safe for employees to work in coffee shops, airports, and more. B2C VPNs, on the other hand, protect data for personal use.
Can the same VPN be used on multiple devices?
Multiple devices can be connected to the same VPN. However, the more devices connected, the slower the VPN is. This might not be a big deal for tasks that aren’t very demanding on your network, but for more data-intensive tasks, such as streaming video, you may find the slowdown a significant annoyance.
How does a VPN change my location?
Via the tunneling and encryption procedure described above, VPNs essentially temporarily replace your IP address to make it look like you are connected to the internet in a different location. All you have to do is open your VPN settings and select the server location you’d like to connect to.
What is a VPN kill switch?
A VPN kill switch is a feature designed to protect your data if you lose connection to your VPN. If you become disconnected from the VPN, the kill switch feature will automatically disconnect you from the internet so your internet traffic is not exposed to the internet service provider.
How a kill switch works:
- The kill switch monitors the status and activity of your VPN connection to ensure your data is safe
- If the kill switch detects a disconnection, it will shut off your device’s internet connection, or disconnect the app you are using from the internet, depending on how you have it set up.
The Impact of AI on The Capabilities of VPN for Government Agencies
Artificial Intelligence is a rapidly expanding technology that has implications for cybersecurity and privacy. The intersection of AI and VPN unlocks new opportunities for securing private government information.
Enhanced Security Capabilities:
AI-driven security mechanisms play a pivotal role in protecting a VPN for government from cyber threats. By using machine learning algorithms and behavioral analysis techniques, VPNs can detect and mitigate security breaches in real time, defending against cyberattacks and intrusion attempts.
- Threat Detection and Prevention: AI-powered threat detection systems can monitor network traffic patterns, analyzing large amounts of data to identify abnormal behavior indicative of potential security threats. These systems can distinguish between legitimate user activities and malicious actions, enabling prompt detection and mitigation of cyber threats before they escalate into full-scale attacks.
- Detecting Unusual Activity: AI algorithms can identify deviations from normal network behavior, such as unusual spikes in traffic volume or unauthorized access attempts, which may signify security breaches or data exfiltration attempts. By flagging suspicious activities in real time, AI-driven anomaly detection systems empower VPNs to respond swiftly and decisively to emerging threats, minimizing the risk of data breaches and network intrusions.
- Malware Detection and Mitigation: AI-powered malware detection tools employ machine learning algorithms to analyze code, enabling rapid identification and containment of malware infections within VPN networks. These tools can detect previously unseen malware variants, enhancing the overall security of VPNs
Privacy Preservation:
AI-powered privacy enhancements enable VPN users to safeguard their online anonymity, protect sensitive information, and mitigate the risk of data exposure in an increasingly interconnected digital ecosystem. By leveraging advanced encryption techniques, anonymization protocols, and privacy-preserving technologies, VPN providers can offer robust privacy protections that shield user data from unauthorized access and surveillance.
- Anonymization: AI-powered anonymization enables VPN users to conceal their identities and online activities, preserving anonymity and protecting sensitive information. Using AI-based routing, AI-driven anonymization techniques can help prevent traffic analysis attacks.
- Privacy-Preserving Data Analytics: AI-driven privacy-preserving data analytics enable VPNs to perform advanced analytics on encrypted user data without compromising privacy or exposing sensitive information. VPN providers can extract valuable insights from encrypted data by using federated learning, differential privacy, and secure multiparty computation.
- Adversarial Defense Mechanisms: AI-powered adversarial defense mechanisms detect and mitigate privacy attacks targeting VPN users, which could include traffic correlation attacks, fingerprinting attacks, and de-anonymization attacks. By taking actions such as introducing perturbations into encrypted traffic and employing countermeasures against adversarial techniques, VPN providers can enhance the robustness of privacy protections and mitigate the risk of privacy breaches.
Performance Optimization and Resource Allocation:
AI-driven performance optimization techniques can enhance the efficiency, scalability, and responsiveness of a VPN for your agency, ensuring optimal resource utilization and seamless user experiences. By utilizing AI-based attributes such as machine learning algorithms and predictive analytics, VPNs can optimize network throughput and dynamically adapt to fluctuating traffic demands.
- Dynamic Routing and Load Balancing: AI algorithms can optimize traffic distribution across VPN servers to minimize congestion and improve network performance. These algorithms can analyze real-time network metrics, which could include the status of the server, bandwidth utilization, and latency, to route traffic along the most efficient paths.
- Predictive Resource Allocation: AI-driven predictive analytics models can forecast future traffic patterns, user demand, and network utilization trends, enabling VPN providers to allocate resources proactively and anticipate increased demand. For example AI could predict peak traffic periods and optimize resource utilization to ensure optimal performance and responsiveness.
- Quality of Service (QoS) Optimization: AI-powered QoS optimization mechanisms could prioritize critical network traffic, such as real-time voice and video communications. By adjusting traffic prioritization based on network conditions, VPN users could optimize QoS parameters and enhance overall service quality.
User Authentication and Access Control:
AI-driven authentication mechanisms enhance the security and usability of VPN access controls, enabling seamless user authentication, identity verification, and access management across diverse network environments. By leveraging biometric authentication, behavioral analysis, and adaptive access control mechanisms, VPN providers can strengthen user authentication processes, mitigate the risk of credential theft, and help prevent unauthorized access to VPN resources.
- Biometric Authentication: AI-powered biometric authentication systems authenticate users based on unique characteristics, such as fingerprints, facial features, or eye patterns, enhancing the security and convenience of VPN access controls. By integrating biometric authentication into VPN client applications, users can securely authenticate themselves without relying on traditional passwords or credentials.
- Behavioral Analysis: AI-driven behavioral analysis techniques analyze user user behavior patterns to establish a unique behavioral profile for each user, enabling continuous authentication and adaptive access control. By comparing real-time user behavior against established baseline profiles, VPN providers can detect anomalous activities, identify potential security threats, and prompt additional authentication measures when necessary.
- Adaptive Access Control: AI-powered adaptive access control mechanisms can dynamically adjust access privileges based on user behavior, device characteristics, and contextual factors, minimizing the risk of unauthorized access to VPN resources. By leveraging machine learning algorithms and policy-based enforcement rules, VPN providers can enforce access controls, restrict privileged actions, and prevent security breaches resulting from compromised credentials or insider threats.
- Multi-Factor Authentication (MFA): MFA remains an effective component of cybersecurity, and AI-driven MFA solutions can enhance the security of VPN access controls.
The Importance of a VPN for Government Agencies: 2024 Predictions
VPNs have not only become more accessible and popular recently, but have become an integral part of internet use. Nearly one-third of the world’s internet users rely on a VPN when accessing the internet. This encompasses 1.6 billion individuals. The worldwide market for VPNs is predicted to grow at a compound annual growth rate of 15.1%. You can also expect to see more efficient security and data protection as VPNs evolve with more recent technologies, such as AI.
Here are some additional recent VPN trends:
- VPN usage in the United States has increased from 24.7% in 2020 to 33% in 2023.
- 80% of people who use VPNs do so for increased security.
- Over 50% of people who use a VPN use it in their workplace.
- 77% of people who used VPNs used them for work on a near-daily basis in 2023.
- VPNs are more popular among iOS users versus Android users.
- Within the first 6 months of 2023, there were 130 million downloads.
- Middle Eastern countries like Qatar and UAE are experiencing a rapid rise in VPN usage.
- South Africa, Japan and Kenya had the lowest VPN adoption rate in 2023.
Ultimately, it can be expected that usage of a VPN in government agencies will continue to remain a relevant cybersecurity precautionary measure in 2024. As the likelihood of cyberattacks increases, it becomes more important than ever to utilize a VPN to protect important data and information.
WHAT THIS MEANS FOR GOVERNMENT WORKERS
If you’re just starting to consider remote work, the best option is to see if your agency has a work-from-home program with government-issued devices. In this case, you should only have to deal with securing communications on the device. As outlined above, one excellent security measure for this is using a VPN your government agency approves or provides for your use.
WHAT THIS MEANS FOR GOVERNMENT CONTRACTORS
For contractors, you will have to follow all regulations that the agency you work for requires.
A company that contracts for the government must already utilize data outside of government networks. Your organization’s on-premises security should already meet these requirements, so work with your IT department to learn how these measures can be replicated or adapted for remote work.
Using a VPN for government work outside of your company’s network is a huge added security feature when it comes to keeping data private.
The Future of VPNs

The use of VPNs has been increasing over the years, but it is still relatively low in the United States compared to other countries. However, usage has been changing as the percentage of people teleworking has fluctuated, both in the private sector and for the government.
At one point in 2020, the State Department, General Services Administration, Department of Housing and Urban Development, Department of Energy, and Small Business Administration were all reported to support at least 85% telework. Additionally, the DoD announced there were 900,000 users on its remote work system. When it comes to VPN usage specifically during the pandemic, the Department of Homeland Security experienced a 483% increase in VPNs for government work.
While not every change from the pandemic has lasted, many major corporations have already decided to allow employees to start working remotely permanently or on a hybrid model. The importance of VPNs has changed significantly since telework became part of the new normal.
The future of VPNs could take several different forms, starting with the likelihood that the increased use of VPNs overall could be the push needed to increase the use of software-based VPN tech, along with phasing out the use of hardware VPNs. More AI and machine learning could also be applied to security functions of VPNs to increase their effectiveness or offer new features.
CONTACT US FOR HELP USING A VPN FOR GOVERNMENT WORK
Now that you are familiar with the advantages of using a VPN for government agencies, you need a dependable partner to walk you through the process and monitor your VPN moving forward. As a veteran-owned company that often works with the government, Sentient Digital knows security is of the utmost importance.
Our team has proven experience managing VPNs for government clients. To learn more about protecting your data and getting started with a VPN, contact us now.




