As data breaches continue to plague organizations at all levels and in all industries, there are 4 important types of data breaches to know in 2022 to keep your information safe:
- Ransomware Attacks
- XSS Attacks
- Man-in-the-Middle Attacks
- SQL Injection Attacks
Although these data breaches may involve criminals making complex maneuvers, a basic understanding of the structure of these attacks may be critical to increasing the security of your organization. Current events illustrate their significance.
Around the world, the security of data remains a paramount issue, particularly as the war between Russia and Ukraine has included a significant cyber component, causing U.S. officials to express their concern. Meanwhile, in the realm of business, as recently as 2020, a hacking group called ShinyHunters leaked 386 million consumer data files from 18 companies on the dark web for free. With large-scale data breaches like this occurring more frequently, enterprises both big and small should know about the top tactics that cyber criminals are using to access confidential business and client information.
Keep reading to learn about 4 main types of data breaches that are threatening today’s enterprises and how to safeguard your organization’s data systems.
WHAT CONSTITUTES A DATA BREACH?
While data breaches against government agencies and businesses are becoming increasingly common, many people still don’t know exactly what defines a data breach. A data breach is any cyber incident in which the privacy of a data system has been compromised, causing an individual or organization to no longer have control over their data. Classifying an incident as a data breach does not necessarily indicate that any data has been sold or leaked to outside parties, though this is a common occurrence in many modern data breaches.
Data Breaches Matter More Than Ever in 2022
The war between Russia and Ukraine has elevated the issue of data breaches to the forefront of many organizations’ cybersecurity concerns. Prior to physically attacking Ukraine, Russia launched a large cyberattack against Ukrainian government agencies that likely gave its leaders knowledge of people’s locations, among other pieces of information that may have proved valuable in planning attacks.
However, on the other side of the war, Ukraine reportedly has also conducted successful cyber attacks against Russia. In these attacks, Ukrainian IT-industry volunteers have accessed and published Russian soldiers’ personal information, as well as knocking out entire websites.
These events have shown that even government and military websites, which one would imagine to be among the most secure in the world, still fall victim to data breaches. How much more vulnerable might your organization’s information be without a deliberate effort to protect it?
Given this information, it makes sense that the first quarter of 2022 saw a 14% increase above the first quarter of 2021, which was in itself a record-breaking year for data breaches. By educating yourself about the types of data breaches, you can take better steps to protect your organization from cyber attacks.
4 TYPES OF DATA BREACHES
Though there are many types of data breaches that today’s cyber criminals use to gain access to an enterprise’s private information, some are favored more than others. Ransomware, XSS, man-in-the-middle, and SQL injection attacks have been among the most dangerous and prevalent types of data breaches used in recent years. Knowing the details of these attacks can help you improve your defenses against them as well as prepare to repair the damage caused should you find yourself the victim of any of these breach types.
1. RANSOMWARE ATTACKS
Ransomware attacks cost all kinds of organizations immense amounts of money every year, and recently more than half of all medium-sized and large U.S. businesses surveyed reported a ransomware attack in the last 12 months. The average remediation costs for a company doubled from 2019 to 2020. As ransomware attacks become even more widespread, more sophisticated, and more damaging, enterprise leaders need to keep this type of data breach in mind when considering their cybersecurity.
The word “ransomware” is the combination of “ransom” and “malware,” which describes the shape and purpose of these attacks. Ransomware is a specific type of malware that blocks authorized user access to data systems and files, demanding payment in exchange for regaining this access. Both big and small businesses have been targeted by ransomware in recent years, so every business needs to consider itself at risk.

Varieties of Ransomware Attacks
Two of the more serious and common varieties of ransomware are locker ransomware and crypto ransomware. In a locker ransomware attack, a user will be locked out of their computer after opening a file or link that was infected with malware. In a crypto ransomware attack, hackers will encrypt specific files in order to block user access to them.
While both types of ransomware can be especially damaging to an organization’s finances and data safety, crypto ransomware attacks indicate that the attackers have already gained direct access to private data files. Protecting your sensitive information against these and other types of ransomware attacks is a critical component of modern cybersecurity.
Examples of Ransomware Attacks
Recent examples of ransomware attacks illustrate the severity of this problem. In 2019, a number of high-profile examples of ransomware attacks against local governments made headlines, including in our home state of Louisiana, 22 cities in Texas, Baltimore, and many others.
In particular, attacks against school districts have been increasing. Schools tend to be very open with the public and lack the resources to implement much cybersecurity, making them prime targets. With many schools transitioning to distance learning for the first time, this trend is sure to continue in 2022. In fact, the FBI has already issued a warning to K-12 schools about the rising threat of ransomware attacks.
Although the recent ShinyHunter leaks were not intended to be leveraged for ransom, someone claiming to belong to the hacking group told WIRED, “It’s just a way to make money, but if companies are afraid and want their database taken off the market, they can contact me for an agreement, it has been done recently and both sides were satisfied.”
2. XSS ATTACKS

XSS attacks have become one of the most widely used types of data breaches in recent years. A cross-site scripting, or XSS, attack occurs when cyberattackers are able to insert a malicious script into a specific webpage’s HTML body that may essentially allow them to pose as a person entitled to access certain information, or allow them to steal information by observing what a user is doing. When an internet user accesses the infected webpage, the malicious script can then be executed against the web user’s browser. This can give the attacker direct access to the victim’s web browser and its data.
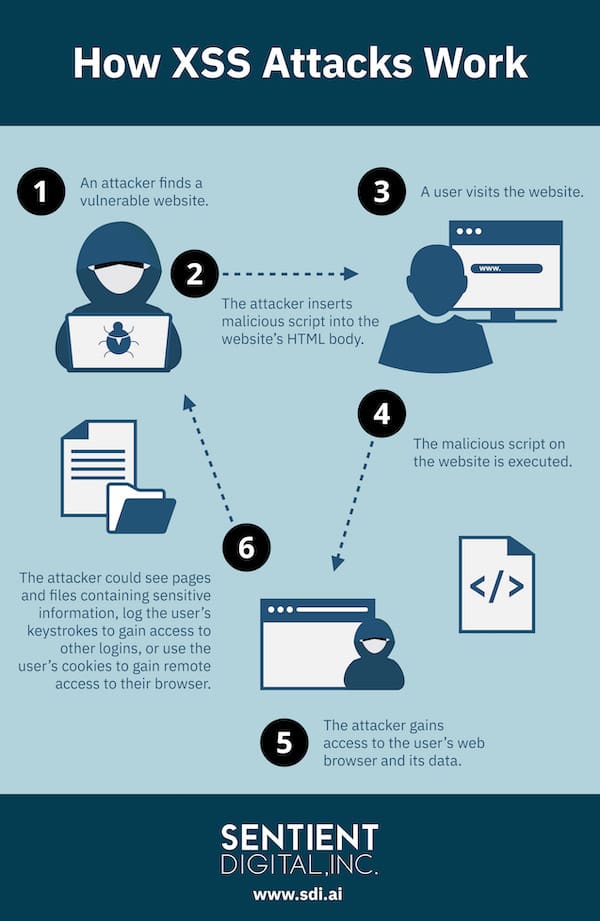
Learn more about how XSS attacks and other types of data breaches work below! Please feel free to share our infographic on social media, or copy and paste the code below to embed it on your website:
<img src="http://bit.ly/typesofdatabreachestoknowin2020">
<p>How XSS Attacks Work - An infographic by the team at <a href="https://sdi.ai/">Sentient Digital, Inc.</a></p>There are multiple ways that cyber criminals can use an XSS attack to breach an organization’s data security. The attacker might take screenshots of pages and files containing confidential information. They might log keystrokes to gain access to other logins. Or they might utilize cookies to engage in session hijacking, in which the attacker gains remote access to the infected web browser. From this point, the hacker may perform any actions that would be available during an authenticated web session.
Example of XSS Attacks
For larger organizations, XSS attacks are especially worrisome because of the prevalence of single sign-on systems (SSOs).
SSOs grant a user access to multiple web applications at once through a single username and password. A successful XSS attack against an SSO system can grant a cyber criminal access to an even wider variety of applications and private user data.
In 2019, for example, a cybersecurity firm discovered a large vulnerability in the popular online game Fortnite. The vulnerability could allow hackers to utilize an XSS attack against the game’s SSO implementation. If successful, such an attack could give hackers access to the login credentials of a single player’s Facebook, Xbox, Playstation, Nintendo, and Google accounts.
3. MAN-IN-THE-MIDDLE ATTACKS

In a man-in-the-middle (MITM) attack, a cyberattacker will intercept communications between two parties in order to gain access to information, such as logins, key dates, file locations, and more. In 2018, MITM attempts were associated with 35% of all security exploits, making them one of the more common types of data breaches organizations should protect against.
Unsecured public Wi-Fi tends to facilitate these attacks. However, researchers have also identified vulnerabilities that could be exploited using man-in-the-middle attacks in 3G, 4G, and 5G wireless networks. Mobile devices and mobile apps are especially at risk of MITM attacks as well. These mobile-based attacks present an even bigger threat to companies whose employees are working from home or must frequently travel for work, where working from phones becomes more common.
Varieties of Man-in-the-Middle Attacks
Traditional man-in-the-middle attacks require a cyber criminal to access an unsecured Wi-Fi network, such as a mobile hotspot, a home internet connection, or a public Wi-Fi network that the attacker has set up themselves. Once users begin utilizing the vulnerable network, the hacker can access any data that is transmitted through the network. From there, they may insert malicious code into network-accessed websites, which can yield further access to a specific network user’s computer.
A man-in-the-browser (MITB) attack is another type of man-in-the-middle attack. With MITB attacks, a cyber attacker may pose as another employee, third-party vendor, or professional entity through phishing emails, a common catalyst for cyberattacks. From there, the hacker may ask the victim to enter sensitive login information or share classified files under false pretenses.
Another MITM strategy involves setting up websites that closely mimic the design and interface of a specific online service provider. This method can trick even regular site users into entering their login credentials.
Examples of Man-in-the-Middle Attacks
Man-in-the-middle attacks actually have pre-digital origins, essentially occurring throughout history. One of the earliest MITM attacks on record occurred in the late-16th century. It involved the interception of letters related to an assassination plot against Queen Elizabeth I of England.
Even in their contemporary, digital context, there are examples of man-in-the-middle attacks that have been just as ambitious. Previously, Russian spies attempted an MITM attack on the headquarters of the Organization for the Prohibition of Chemical Weapons (OPCW). And as recently as 2019, the national government of Kazakhstan attempted to introduce an internet surveillance system which would have allowed government agencies to utilize MITM attack techniques against citizens.
4. SQL INJECTION ATTACKS

SQL, or Structured Query Language, is a programming language commonly used for web-based data management systems. Constituting 65% of web-based attacks between November 2017 and March 2019, SQL injection attacks have increased significantly in recent years.
In an SQL injection attack, a hacker gains control over a web database in order to tamper with its contents. For example, an attacker can exploit a weakness in a web application’s SQL coding and command the system to “dump” all of its data in a digital location of the hacker’s choosing.
Since SQL injection attacks are a type of data breach in which a cyber attacker can exert complete control over a web-based application, some hackers will also utilize this attack type to destroy a data system entirely.
These attacks rely on vulnerabilities present within a web-based data system’s coding. Auditing existing digital systems and remediating their vulnerabilities is a key part of preventing these and many other types of data breaches.
Examples of SQL Injection Attacks
Previously, this kind of attack has been used against high-profile data management systems at The Wall Street Journal. The American gaming and e-commerce industries in particular have been impacted by the rise of this type of data breach. For example, a New York-based hacker was charged in May 2020 after using SQL injection methods against e-commerce websites to launder over $100 million in Bitcoin.
COMMON VULNERABILITIES LEADING TO DATA BREACHES
All types of data breaches are able to occur because of vulnerabilities present in an organization’s digital systems and cybersecurity protocols. Some of the most common IT vulnerabilities that lead to data breaches include:
- Weak username and password guidelines, including a lack of two-factor authentication, the use of social security numbers in login credentials, and not requiring employees to update their login credentials after a set period of time.
- Lack of vulnerability and compliance management (VCM), which describes the regular monitoring and auditing of IT infrastructure and digital systems, as well as the implementation of proactive cybersecurity measures.
- Lack of employee education on basic cybersecurity practices, such as logging out of key accounts before leaving your desk and only accessing confidential files while connected to the organization’s private network.
Implementing steps to improve in these areas is an excellent start to protecting your organization against data breaches. For example, ensure that all employees understand that protecting the company from data breaches requires everyone’s adherence to security policies. Employees should receive specific instructions on mitigating risks, but also how to report anything that appears suspicious or known security breaches. Remember that data breaches continue to evolve and therefore an organization must continually update its policies and continually update employee education.
PROTECT AGAINST ALL TYPES OF DATA BREACHES WITH SENTIENT DIGITAL, INC.

Data breaches remain a major threat to all organizations in 2022 and although knowing what to watch out for certainly helps, you may need outside support to ensure that you effectively protect your operations. Sentient Digital, Inc. is a veteran-owned technology solutions company dedicated to completing IT projects, providing technology services, and supplying supplemental staff for both commercial and governmental organizations. We pride ourselves on leveraging our knowledge, skills, and experience to obtain results for our clients. We specialize in cybersecurity, artificial intelligence and machine learning, R&D, government contracting, systems engineering, data and enterprise architecture, data loss and fraud prevention, cloud services, workforce solutions, and more.
Looking for expert help on an upcoming tech project? Need ongoing managed IT services to protect your organization from data breaches? Contact Sentient Digital, Inc. today to learn more about what we can do for you!
For IT professionals looking to make the next step in their career, we invite you to visit our careers page to learn more about our professional opportunities in software development, systems engineering, information technology, and more.




